If you’ve been around health IT long enough, you’ve heard this one before: Rails exist; usage lags.
The idea sounded revolutionary back in 2020. CMS’s Patient Access Rule (CMS-9115) opened consumer pipes; CMS‑0057 (2024) shifts value into prior auth and clinical workflows.
The regulatory drumbeat is steady:
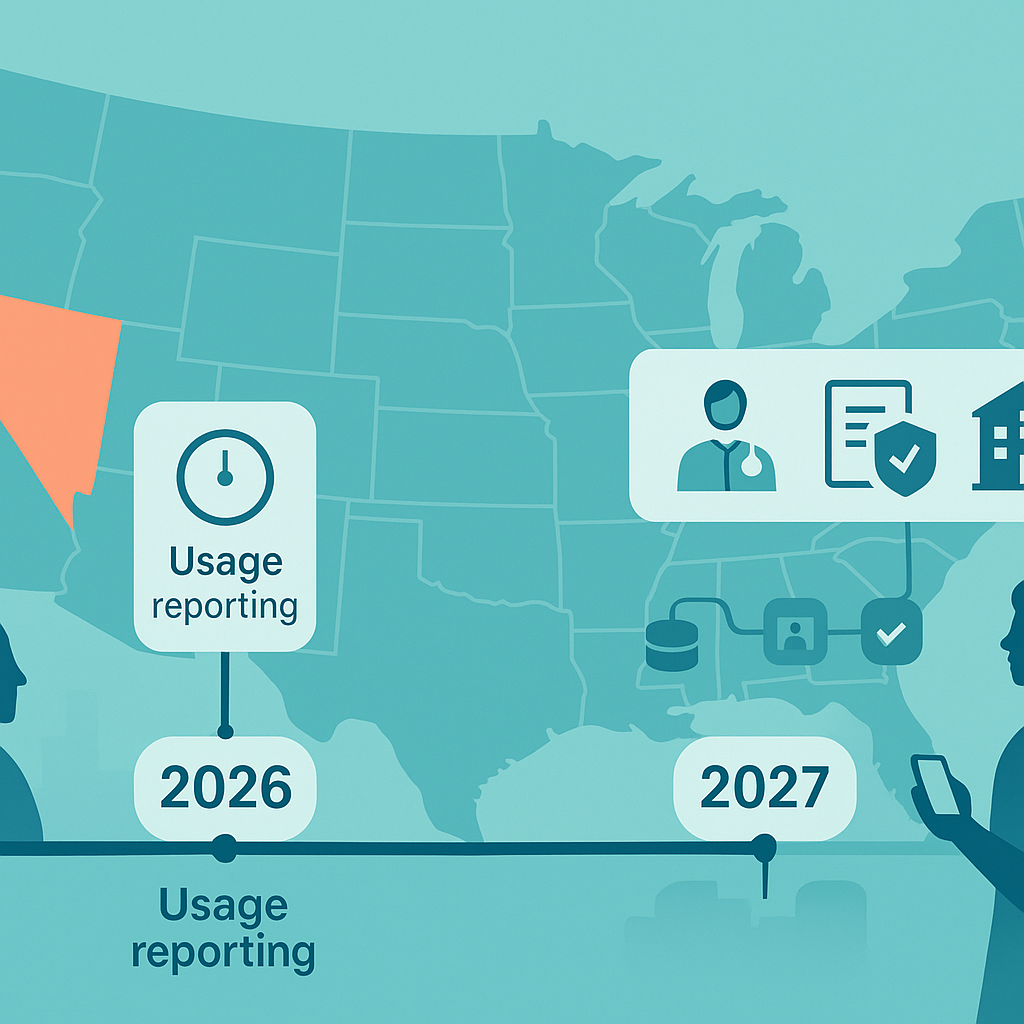
- Jan 1, 2026: payers report Patient Access usage + faster PA SLAs.
- Jan 1, 2027: Provider Access, Prior Auth, enhanced Patient Access, and Payer‑to‑Payer go live across MA/Medicaid/QHPs.
On paper, that’s a big deal. In practice? Nearly half of targeted payer endpoints still don’t have a live Patient Access API. Only about one-third cover all lines of business, and usage numbers are… well, let’s just say Carequality moves 940 million clinical documents a month, while patient-mediated API pulls number in the hundreds per plan.
Awareness is low, onboarding is clunky, and variability slows first‑pull success.
And yet, this is precisely why they matter now. The legal scaffolding is in place, a small number of states have extended scope to commercial lines, and CMS is dangling carrots (and swinging sticks).
If you can bridge that gap — turn the regulatory requirement into a product patients actually want to use — you’re not just ahead of compliance. You’re ahead of the market.
Key Takeaways
- Deadlines drive strategy, not hype. 2026 forces usage reporting and faster PA decisions; 2027 lights up Provider Access, Prior Auth, enhanced Patient Access, and Payer-to-Payer (FHIR R4). Translation: plan a 2026 ops lift and a 2027 API/product lift.
- Coverage is patchy; adoption lags. Only California and Tennessee mandate APIs across commercial lines; elsewhere it’s a patchwork. Meanwhile, many endpoints aren’t live and patient-mediated pulls remain tiny versus HIE traffic. Pick markets accordingly.
- Buy connectivity; own differentiation. Use aggregators/networks to move fast, but win on reconciliation (EOB math), identity, consent UX, and “invisible” retrieval. Instrument KPIs from day one.
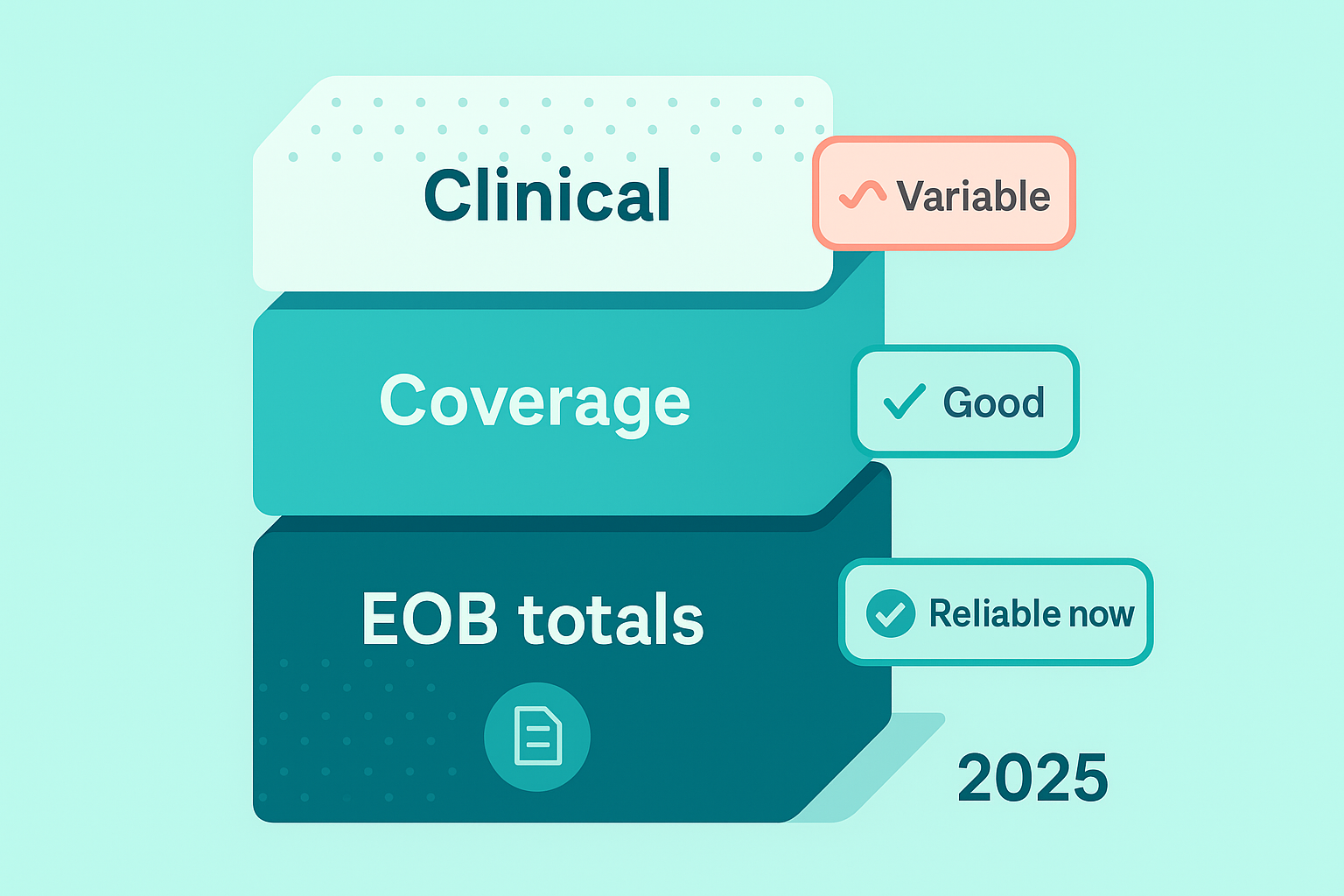
- Claims ≠ clinical—merge intentionally. Payer APIs give longitudinal “what happened/what it cost”; EHR/HIE rails give encounter detail. Use EOB totals as your financial source of truth and US Core for clinical depth; show provenance.
Table of Contents
- Legislative Landscape: What Healthcare Execs Need to Know
- Patient-Mediated APIs vs. Traditional HIE APIs: what’s the real difference?
- Adoption Reality Check: Where We Stand in 2025
- Practical Use Cases: Untapped Opportunities for Innovators
- Data Availability, for Real: What You Can Ship in 2025 (without promising magic)
- Building Realistic Solutions: from Regulation to Revenue
Legislative Landscape: What Healthcare Execs Need to Know
Short version: CMS moved from “open the vault” to “wire it into workflow.” States? Mostly sitting on the sidelines—except California and Tennessee, which dragged commercial plans into scope. Everyone else is watching the federal clock.
The Federal Shift: from Access to Automation
- Phase 1 (2020 – CMS-9115-F): Patient Access + Provider Directory APIs; Payer-to-Payer was required but later put under enforcement discretion.
- Phase 2 (2024 – CMS-0057-F): Adds Provider Access API and Prior Authorization API, revives Payer-to-Payer, and enhances Patient Access to include prior-auth details—because data only matters if it reduces admin pain. Estimated $15–$16B savings over 10 years, primarily for providers.
Deadlines you can’t miss:
- Jan 1, 2026: Faster PA decisions (72h urgent / 7d standard) + denial reasons; start collecting Patient Access API usage for CMS (first report due Mar 31, 2026).
- Jan 1, 2027: Go live with Provider Access, Prior Auth, enhanced Patient Access (incl. PA), Payer-to-Payer—FHIR R4 across the board. Also, provider incentives via a new MIPS PI measure; HIPAA “safe harbor” lets you prioritize FHIR over the legacy X12 278.
Why this matters: CMS isn’t just publishing spec sheets; they’re forcing modernization of prior auth and payer-provider data plumbing so the value shows up in the EHR/ordering workflow—not another portal.
States: Reality vs. Rumor
- Hard reality (mid-2025): Only two states mandate Patient Access / Directory / Payer-to-Payer APIs across all lines of business, including commercial: California (SB 1419, effective Jan 1, 2025) and Tennessee (SB 2012, effective May 6, 2024). Both align to CMS technical standards (FHIR R4 + CARIN/PDex).
- California’s broader play: AB 133 extends a statewide Data Exchange Framework; smaller entities get until Jan 31, 2026.
- Everywhere else: Lots of privacy talk and prior-auth reform, little to no commercial-plan API mandates yet. Expect a patchwork until more states follow—or the feds do it for them.
- Correcting the record: You may hear “NY/GA/TX are in,” but the enacted, all-lines API mandates today are CA and TN—full stop.
Requirements vs. Reality (and what it means for product strategy)
- Federal rails are real, but value concentrates as PA/Provider APIs arrive in 2027. Plan for two stages: (1) operational PA changes by 2026; (2) full API lift by 2027.
- Commercial coverage varies by zip code: If your target members are in CA/TN, you can assume commercial‑line API access; outside those states, your Patient Access strategy mainly rides MA/Medicaid/QHPs or voluntary adoption.
- Provider workflows are the prize: The Prior Auth API (plus Provider Access) is where the ROI shows up. Align to 2027 FHIR APIs + the new MIPS PI measure.
- Architecture note: design for reuse (Stars/HEDIS, risk, population health) while you implement compliance.
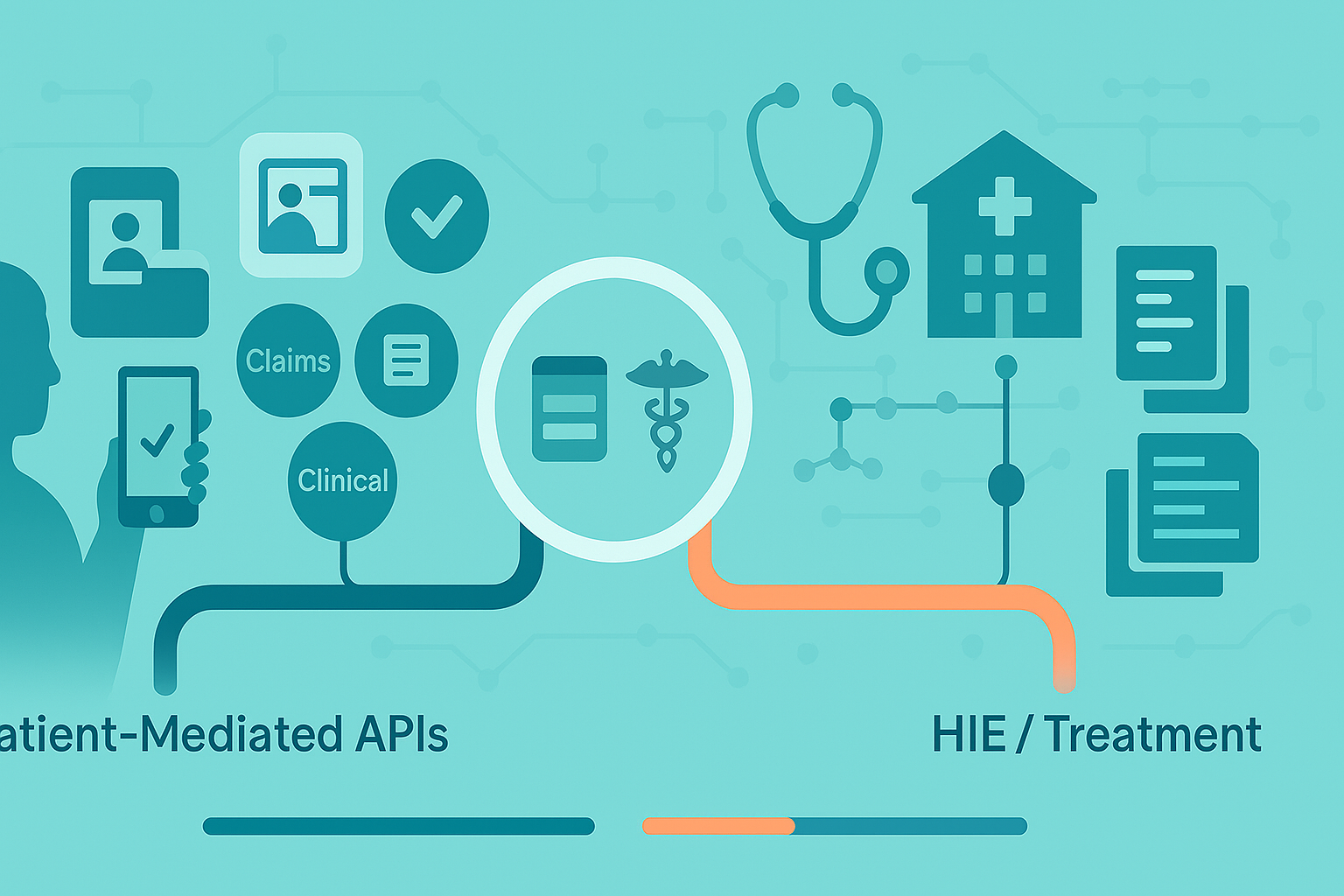
Patient-Mediated APIs vs. Traditional HIE APIs: what’s the real difference?
Short take: There are two parallel rails for patient data—and they are not interchangeable. Payer rails are longitudinal + financial; provider/EHR rails are clinically deep but siloed. Plan for an intentionally combined view; no single vendor yields a fully unified record today.
What “Patient-Mediated (Non-Treatment) APIs” Actually Are
- Payer Patient Access APIs (CARIN/Blue Button on FHIR): returns adjudicated claims with cost-sharing (deductible, copay, coinsurance, member liability) and linked Coverage details. This is your cleanest source of “what happened and who owes what.”
- EHR patient-mediated APIs (US Core on FHIR): returns clinical content (labs, vitals, problems, meds, notes) for encounters inside that one health system’s EHR—deep but siloed. Also, “Must Support ≠ Must Have”: even compliant APIs can return empty fields when the source data lives only in free-text.
How They Differ from HIE/Treatment-Purpose Exchange
HIE/Network rails (Carequality/CommonWell/TEFCA) are treatment-purpose and move enormous volumes of clinical docs system-to-system; patient-mediated pulls are consented by the patient and flow through payer/EHR APIs instead.
Aggregators on the HIE side parse C-CDA to FHIR; payer-side pipes are natively claims-first. Different pipes, different payloads, different latencies.
Data Reality (strengths & limits you can bank on)
- Payer stream (strengths): longitudinal record of billed care + cost-share math (EOB total and item.adjudication are the reliable fields developers actually use). Great as a “record locator” to discover where to fetch clinical detail next.
- Payer stream (limits): only what the plan maintains in structured form; prior-auth details won’t consistently surface in Patient Access until the 2027 uplift; Payer-to-Payer explicitly excludes cost-sharing.
- EHR stream (strengths): rich encounter-level detail (labs, notes, vitals) mapped to USCDI via US Core.
- EHR stream (limits): system-bound and riddled with data-quality gaps; if it’s not discretely captured, the API won’t hand it to you. Expect missing problems, messy coding, and note blobs.
Who Operates in Each Category (so you pick the right partner)
Payer/claims specialists
Flexpa—CARIN/Blue Button, EOB-first, explicit normalization of financial elements; no provider-side clinical aggregation.
Clinical/HIE specialists
Particle Health, Health Gorilla—network queries (Carequality/CommonWell), C-CDA → FHIR parsing; not claims/EOB-centric.
Direct payer baseline
Wellpoint’s dev portal confirms CARIN R4 for Patient Access (claims + clinical they maintain). Useful as a “this is what large plans actually expose” reference.
Broader integration platforms / adjacent
Redox, 1up, Zus, Metriport, OneRecord, plus prior-auth/eligibility specialists (Cohere, pVerify, Eligible, Change, etc.). Match the tool to the rail you need; marketing language blurs the lines, the underlying source doesn’t.
Where to Use Which (concrete scenarios)
- Clinical trials & research onboarding: Use EHR/HIE rails to assemble clinical history; augment with payer claims for encounter completeness and eligibility context.
- Patient engagement & transparency apps: Lead with payer Patient Access for what happened + what it cost, then deep-link into EHR APIs for recent labs/notes the moment the user authorizes the health-system connection.
- Financial responsibility hubs: Payer first (EOB totals, member liability, copays/deductibles) with clear disclaimers for provider-issued invoices; optionally pull EHR encounters to reconcile “what care drove this bill.”
Adoption Reality Check: Where We Stand in 2025
Two things can be true at once: the regulatory rails are here, and consumer demand hasn’t shown up yet. Deployment is uneven, but the bigger story is utilization: utilization remains in the hundreds per plan; most patients still don’t aggregate their records.
What’s Actually Blocking Uptake (it’s not just the tech)
- Awareness & trust are low; when marketed, usage spikes.
- Auth fatigue: duplicate credentials, awkward consent, short‑lived tokens; design recovery into the happy path.
- Implementation drift: variable OAuth/scopes/payloads; empty responses/timeouts on first connection; per‑payer app registration throttles supply.
- Distribution skew: mainstream aggregators lean provider APIs; payer connectors are long tail.
Field Notes (from the folks doing the work)
Traffic today is platform-led. A handful of aggregators account for most real usage, which means your adoption curve will initially look like their channel strategy, not yours. Standards hygiene moves mountains: publishing a proper .well-known, aligning scopes, and returning consistent errors sounds boring until it cuts your integration lead time in half.
And yes—policy tailwinds are coming: usage reporting in 2026 will spotlight laggards; Provider/PA APIs in 2027 should shift value into clinician workflows where patients actually feel the impact downstream.
How to Win Anyway (pragmatic playbooks)
- Plans: Treat Patient Access as a product, not a checkbox. Budget for marketing + identity (education campaigns, better proofing), and tie the 2026 reporting work to a 2027 “clean room” of metrics you’re proud to publish.
- Provider-facing vendors: Lead with an ePA-in-the-EHR story. If you shorten prior-auth cycle times and reduce denials, you’ll have the clinical attention—and a path to introduce patient-side access without feeling like another portal.
- Consumer apps: Go where coverage is real first (MA/Medicaid/QHP; state-mandated commercial where applicable). Ship forgiveness into the UX: retries, cached partial views (“here’s what we have so far”), and plain-English errors. Build with aggregators now; push payers on conformance as your volume grows so the unit economics improve.
Bottom line: 2025 is the year you stop pitching “we connect to your data” and start proving repeatable retrieval with acceptable friction. The winners won’t be the teams that found the API—they’ll be the ones who made it feel invisible.
Practical Use Cases: Untapped Opportunities for Innovators
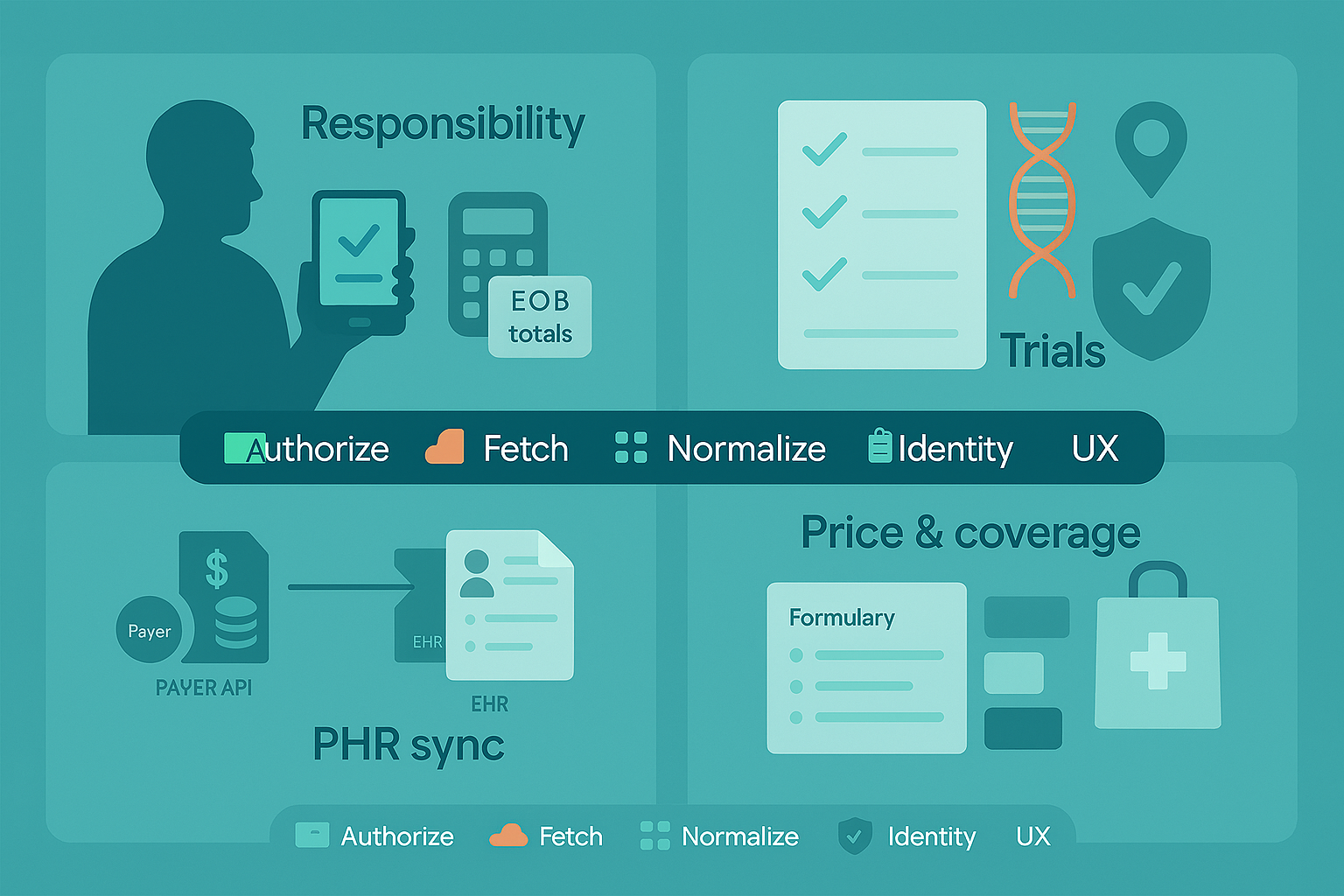
Patient Responsibility Hubs (what happened + what it cost)
What to pull: Start with payer Patient Access (CARIN/Blue Button) and the ExplanationOfBenefit (EOB). Rely on total and item.adjudication for member liability, copays, coinsurance, deductible; it’s the most consistently populated financial payload. Use claims as your record locator to drive targeted EHR fetches only when you need clinical detail.
Build it like this:
- Pull claims → compute what the member owes per encounter.
- When a line looks off, fetch the encounter’s clinical from the health-system’s US Core API to explain the bill in human terms (diagnosis/procedure summary).
- Warn about provider-issued invoices that won’t show up in payer feeds.
Proof it works (directionally): Cedar’s “ClaimSafe”-style pattern reports 40% faster payments, 55% fewer disputes, and $12M admin savings across systems after surfacing coverage gaps in-flow. Treat as directional until you have your own KPIs.
Gotchas: Payer-to-Payer exchange in 2027 excludes cost sharing; don’t expect portability of member-liability across plans. Prior-auth data doesn’t hit Patient Access until Jan 1, 2027; design your UI to show PA status only when available. And remember the CMS “if maintained” caveat—payers aren’t required to parse PDFs into structured fields.
Patient-Driven Consent for Research & Clinical Trials
What to pull: Combine EHR patient-mediated (US Core) for problems, meds, labs, notes with payer claims to find where a patient received care. Use that to reduce chase-lists and pre-fill eligibility questions.
Build it like this:
- Eligibility pre-screen from patient-authorized EHR data; only then hit networks/HIEs for missing pieces.
- If you’re embedding in clinician workflow, wire to CDS-style prompts after the chart opens; if patient-facing, keep consent granular by study arm/data class.
Proof it works (directionally): TrialX-style deployments cite 34% faster screening and 24–50% more eligible matches when tapping FHIR at multiple systems; the ADAPTABLE study reported 11.1% enrollment lift and 92% retention with automated follow-ups. Useful order-of-magnitude targets.
Gotchas: “Must Support ≠ Must Have.” Expect empty fields when sites chart in free text; design tolerances for incomplete data and fall back to C-CDA or DocumentReference when structured isn’t there.
PHRs with Real Portability (beyond a nicer portal)
What to pull: Multi-source US Core (per system) + payer claims for longitudinal “spine.” Use patient-mediated OAuth everywhere; add $match/identity-resolution to reduce duplicate charts.
Build it like this:
- First-run: show instant wins (med list, allergies, last labs) even if some systems are still connecting.
- Background jobs: reconcile problems/meds, de-dupe encounters, and surface explainable discrepancies (e.g., claim without note).
- Export: one-click IPS/share packs for referrals.
Proof it works (directionally): Argonaut-style PHRs report 50% engagement lifts in chronic cohorts and ~38s average record retrieval; VA-style pilots show 73% fewer duplicate tests and 84% satisfaction when patients control outbound sharing. Treat as benchmarks, not promises.
Gotchas: US Core depth is great inside one system but fragmented across many; plan for progressive completeness and show provenance by source so clinicians trust the merge.
What to Ship Next (opinionated)
- Pick one flagship metric per use case (e.g., “% of encounters with computed member liability,” “eligible-to-consented conversion,” “duplicate-test rate”).
- Instrument failure first (timeouts, empty payloads, auth drop-offs) so you can make adoption a math problem, not a vibes problem.
- Design for 2027 uplift now: add PA placeholders and audit trails so you slot in prior-auth data the day it becomes available.
Data Availability, for Real: What You Can Ship in 2025 (without promising magic)
What You Can Bank on (use this for commitments)
- EOB math for money questions. Compute member liability from EOB.total first; fall back to line-level item.adjudication only when totals are missing. Pair each EOB with its Coverage so the cost-share math reflects the correct plan/time period.
- Provider/date truth. EOBs are a dependable record locator (who/when/where). Use them to target any clinical fetches you actually need.
Where Products Break (design around it, don’t explain it)
- Structured gaps are normal. Treat clinical fields as optional at runtime; if the value isn’t there, don’t block the flow—surface provenance and move on.
- Unstructured exists—don’t rely on it. If the only source is a PDF/note, it may not appear via API. Avoid features that depend on NLP to work on day one.
Five Pre-launch Tests That Save Quarters of Rework
- Liability recompute: Given a sample EOB set, your calculator must match the payer’s member-facing totals ≥95% of the time. Flag—and explain—mismatches.
- Coverage join: Every EOB row must resolve to a specific Coverage (historical plan). Break the build if join fails.
- Empty-payload tolerance: Simulate first-connection sparsity; your UI should still render a useful baseline (e.g., last 3 encounters, meds list) without apology screens.
- Error discipline: Normalize OAuth and API errors into 5–7 user-facing states max (retry, re-auth, slow source, locked account, etc.).
- Provenance labels: Every datum shows source + last refreshed. Clinicians trust merges they can audit.
Small Table, Big Decisions
| Product promise | Source of truth | Implementation note |
| “Show me what I owe for that visit.” | EOB total (then item.adjudication) | Compute once, cache, and expose “show-the-math.” |
| “Who/when/where of care.” | EOB header + provider IDs | Use as record locator for any selective clinical fetch. |
| “What exactly happened clinically.” | US Core (per system) | Render progressively; never block on a missing field. |
| “Portable, explainable share pack.” | US Core + EOB | Build an IPS-style export with provenance baked in. |
What Not to Promise (and what to say instead)
- Don’t: “One API = unified clinical + financial.”
Do: “We reconcile payer and EHR feeds and show provenance so you can trust the merge.” - Don’t: “Every charted detail will appear.”
Do: “We surface what’s structured now and fetch documents only when they change a decision.”
Product Framing That Actually Ships
- Financial clarity first: Make “Download EOBs” and “Explain this total” first-class; it builds trust and reduces support tickets.
- Clinically progressive: Prioritize always-useful lists (meds, allergies, last labs) and let completeness improve as users connect more systems.
- Roadmap honesty: Add placeholders for prior-auth artifacts and denial reasons now; wire them in when they’re truly available—no refactors, no backpedaling.
Building Realistic Solutions: from Regulation to Revenue
Executive summary: this is where good intentions die or ship. Below is the how—a reference architecture, a blunt build-vs-buy, a cost sketch your CFO won’t hate, the minimum compliance bar, a KPI ladder, and a 12-week plan that actually lands.
Reference Architecture (Text-First)
Data plane
- Ingress:
- Payer Patient Access (claims/EOB, coverage).
- Patient-mediated EHR (US Core resources).
- Normalization: map inbound payloads to a canonical clinical/financial schema (don’t chase every IG nuance in your app layer). Version the mapper; treat mappings as code with tests.
- Identity resolution: deterministic first (member ID + DOB; MRN + system OID); fall back to probabilistic (name, DOB, phone/email, address). Maintain a golden patient with link provenance.
- Reconciliation services:
- Financial: compute member liability from EOB totals; attach Coverage at time-of-service; surface “show-the-math.”
- Clinical: de-dupe encounters, reconcile problems/meds, label gaps (unknown vs. absent).
- Eventing & retries: queue + idempotency keys; backoff for flaky endpoints; dead-letter with human review.
Control plane
- Consent & scopes: OAuth app registration registry; consent objects are versioned and human-readable (who, what, why, how long).
- Audit: append-only logs (WORM) for who accessed what, when, under which legal basis.
- Secrets & keys: PHI separated from app config; short-lived tokens; KMS-managed keys; least-privilege IAM.
- Observability: golden signals (TTFD—time to first data, first-pull success, P95 retrieval latency, empty-payload rate, OAuth drop-off).
Experience layer
- Responsibility hub UI: balance per encounter → “explain this total” → minimal clinical context.
- Research: pre-screen form prefilled from US Core; explicit per-study consent.
- PHR: progressive disclosure (what we have now / what’s connecting), provenance badges, IPS export.
- 2027 slots: PA status/denial reasons placeholders wired to your model so the moment they’re available, they render without refactor.
Build Vs. Buy (use-case driven)
| Capability | Build (direct to payers/EHRs) | Buy (aggregator/network) | When to prefer it |
| Payer Patient Access connectivity | Zero vendor fees; full control; you own conformance pain and app registrations | Faster market coverage; dev tools; may still require payer registrations per app | Buy to move fast; build once volume justifies owning costs |
| EHR/HIE connectivity (treatment purpose) | High lift; multiple vendors; legal onboarding per system | Established networks (Carequality/CommonWell) + record location, doc conversion | Buy unless you’re a very large provider org |
| Normalization & mapping (CARIN/US Core) | Precise to your model; testable | Accelerated ingestion; less flexible down the line | Build core, buy adapters if needed |
| Identity resolution | Tailored rules; competitive moat if done well | Off-the-shelf MPIs reduce risk but can be $$ | Hybrid: start with vendor MPI; layer your logic |
| Consent & audit | Fine control, cleaner UX | Faster to comply; opinionated flows | Build for UX, buy if timeline is brutal |
| EOB compute & financial UX | Core to differentiation in finance use cases | Few vendors do it well; still explain math yourself | Build (this is product) |
| Prior auth (ePA) workflow | Closer integration with your EHR partner | Vendors exist but focus on provider orgs | Partner; don’t reinvent if you sell to clinics |
Rule of thumb: buy connectivity, own reconciliation, consent UX, and the experience that moves your KPIs.
Cost Model (what you actually pay for)
Direct costs
- Connectivity:
- Payer Patient Access: $0 in access fees, but you’ll pay in engineering time and registrations.
- Clinical networks: per-search / per-document fees, monthly minimums, sometimes tiered by org size.
- Identity proofing/MPI: per-verification or MAU-based.
- Hosting & storage: hot storage for working sets; archive for audit.
- Security & compliance: pen tests, SOC 2, legal counsel, BAAs/DUAs.
Hidden/variable costs
- Per-payer app registration friction: weeks that don’t show on a price sheet.
- Data quality remediation: mapping edge cases, code-system normalization, manual exceptions.
- Support & ops: handling OAuth lockouts, patient identity merges/splits, and provider roster drift.
- Change tax (2027 uplift): budget to light up PA fields without re-plumbing.
Financeable levers
- Shift from per-pull to cached, explainable views (hit APIs less; serve users more).
- Automate first-pull failure recovery (cuts support tickets).
- Make exportable artifacts (IPS/EOB packs) a premium feature in B2B contracts.
Security & Compliance Baseline (the minimum to be boring)
- BAAs everywhere PHI flows (aggregators, IDV, error logging vendor if PHI can leak).
- Consent you can read in court: data classes, duration, revocation mechanics, and purpose (non-treatment) spelled out.
- Audit trails: immutable, queryable; alert on anomalous access.
- Data minimization & retention: ingest what you need; default deletion windows; purge flows.
- Access control: RBAC + break-glass with reason codes; session timeouts.
- Encryption: in transit (TLS 1.2+), at rest (KMS), field-level for high-risk elements.
- Incident response: 1-page runbook; contracts specify notification windows and roles.
If you can’t check these boxes, you don’t have a product—you have a liability.
KPI Ladder (make adoption a math problem)
Weeks 0–4 (can we even pull?)
- Connectivity rate (authorized members with at least one successful pull): target ≥ 70% in pilot.
- First-pull success (no manual intervention): ≥ 60% → instrument causes (OAuth, empty payload, timeout).
- TTFD (median): ≤ 90s from consent to first usable data.
Weeks 5–12 (is it repeatable?)
- Repeat retrieval rate (same member, week-over-week): ≥ 65%.
- P95 retrieval latency: ≤ 3s (from cache) / ≤ 15s (live).
- Finance hub: % encounters with computed liability ≥ 90%; dispute rate trending ↓ 20–30%.
Quarter 2 (does it change outcomes?)
- Engagement: DAU/WAU lift in target cohorts; task completion rate for “explain this charge.”
- Provider-adjacent: when PA lights up, cycle-time delta (submit→decision) and denial rate.
- Support load: OAuth/help-desk tickets per 1k members ↓ month-over-month.
Dashboards: put these on the TV; kill vanity metrics. If it doesn’t move behavior or cost, it’s trivia.
12-Week Implementation Plan (no heroics, just shipping)
Weeks 0–1: foundation & scope
- Finalize use-case MVP (one!) and success metrics from the KPI ladder.
- Choose connectivity approach (buy vs. build); start BAAs, sandbox keys, and payer app registrations.
- Stand up secrets management, audit log store, and a basic consent service.
Weeks 2–4: data plane v1 + skeleton UX
- Build normalization mappers (CARIN EOB totals first; minimal US Core set).
- Implement identity resolution (deterministic rules), provenance tags, and retries/idempotency.
- Ship skeleton UI with provenance badges and “show-the-math” panels.
- Observability: wire TTFD, first-pull success, OAuth drop-off.
Weeks 5–8: pilot
- Onboard a small cohort (100–500 members).
- Iterate on empty-payload handling and error normalization (reduce user-facing states to ≤7).
- Add IPS export and EOB download; close the loop on one support pathway (OAuth lockout).
- Security: run a lightweight pen test; fix the top five findings.
Weeks 9–12: harden & prep scale
- Expand to 2–5k members; performance pass (cache strategy, P95 latency).
- Add probabilistic identity resolution for edge cases; add manual merge/split tooling.
- Lock data retention defaults; finalize incident-response runbook.
- Wire 2027 slots (PA status/denial placeholders) into the data model + UI behind feature flags.
- Run a “go/no-go” against KPI ladder; only expand when first-pull success and computed-liability coverage clear thresholds.
SOW deliverables to bake in: mappings + tests, consent copy + flows, audit log queries, KPI dashboards, runbooks (support, incident), and a “cut list” of non-MVP fields you will not chase.
The Blunt Bits (so no one is surprised later)
- You’ll buy connectivity to go fast and own reconciliation/UX to win.
- Your first-pull will fail more than you like—instrument for it and recover gracefully.
If your roadmap depends on features that don’t exist yet, label them and wire the slots now. You’ll look prescient later instead of wrong.
Want this working in 12 weeks? Grab time with Topflight and leave with a plan, a stack, and a number you can defend. Schedule a discovery call →
Frequently Asked Questions
What should we build vs. buy first?
Buy connectivity (payers/EHR networks) to cover ground quickly; own normalization, identity, EOB compute, consent/audit, and UX. That’s where your moat is.
Which states actually mandate patient access APIs for commercial plans?
As of mid-2025, only California and Tennessee. Expect a patchwork elsewhere until more states or the feds expand scope.
How do patient access APIs different from HIE/treatment exchange?
Patient-mediated rails (payer/EHR APIs) are consented by the patient; payer feeds are claims-first (cost share), EHR feeds are clinical but siloed. HIE rails (Carequality/CommonWell/TEFCA) move huge clinical document volumes for treatment. You need both.
What KPIs prove this is working in the first 12 weeks?
Pilot targets: connectivity rate ≥70%, first-pull success ≥60%, median TTFD ≤90s; then repeat retrieval ≥65% and P95 latency ≤3s (cache)/≤15s (live). Put these on a dashboard and kill vanity metrics.
What can we reliable ship in 2025 - without promising magic?
Bank on EOB totals (with Coverage) for member liability and use EOBs as record locators; treat missing clinical fields as normal and never block the UX—show provenance and move on.