Behavioral health platform development isn’t a shopping trip for video, scheduling, and messaging. It’s a commitment to own workflows, evidence, and revenue under real constraints: HIPAA/Part 2, FHIR pipes that actually move data, denials that spike when documentation slips, and no-shows that wreck staffing.
You need a launch path that proves value fast—measurement-based care without a research lab, clean claims without a billing war room, and safety workflows that work at 2 a.m.
The playbook here is pragmatic: scope the care model before code, wire a minimum viable data model that survives EHR reality, treat compliance as product, choose an architecture that scales without a platform rewrite, and assemble HIPAA-ready components where they’re commodities—keeping your differentiators custom.
If it doesn’t move outcomes, throughput, or collections, it’s not in the first release.
Key Takeaways
- Platform ≠ app. Own the clinical loop and the revenue loop: instrument PHQ-9/GAD-7, tie every note to plans/goals, keep HIPAA/Part 2 + consent/audit trails first-class, and design for payer acceptance from day one.
- Shipable architecture wins. Start with a lean FHIR-anchored data model (Episode/Encounter, Questionnaire→Observation, CarePlan/Goal), event-driven integrations, multi-tenant isolation, and zero-trust; assemble HIPAA components, build your differentiators. This scales cleanly from web/mobile into an online therapy platform without rewrites.
- Execution = MVP → proof → scale. Launch the essentials (video, scheduling, assessments, SOAP, portal, basic billing), then add groups, eRx, full RCM, outcomes dashboards, safety-by-design, and responsible AI (assist, not direct). Track reimbursement, engagement, and outcome deltas to improve mental health services and negotiate better payer terms.
Table of Contents
- Platform, Not “an App”: Outcomes You Must Own
- Define Scope and Care Model before Code
- Minimum-Viable Clinical Workflows and Data Model
- Compliance You Can’t Fake
- Reference Architecture for BH Platforms
- Core Feature Set by Phase (MVP → Scale)
- Interoperability Playbook (EHR and beyond)
- Safety and Risk Management by Design
- Build vs Buy vs Assemble (reusable HIPAA components)
- Responsible AI (without tripping FDA)
- How Topflight Can Help You Develop a Behavioral Health Platform
Platform, Not “an App”: Outcomes You Must Own
If you’re doing mental health platform development to ship another Zoom wrapper, skip this blog. A behavioral health platform isn’t a feature buffet; it’s a care delivery system that moves clinical and financial needles—and can prove it.
A platform means workflows + data + operations + compliance moving in lockstep. Intake isn’t a form; it’s the start of an outcomes trail. Notes aren’t text; they’re structured evidence for payers and quality teams. “Messaging” isn’t a chat bubble; it’s a risk-aware channel with audit, escalation, and consent baked in.
What that looks like in practice:
- Intake → assessment → session → documentation → billing → outcomes, instrumented end-to-end.
- Standardized measures (e.g., PHQ-9, GAD-7, PROMIS where relevant) captured at predictable intervals.
- Data model that ties a goal/treatment plan to encounters, clinician time, and claims.
Own These Four Outcomes (or it’s not a platform)
- Symptom change: track deltas on validated scales over time, not just one-off scores.
- Attendance & access: no-show rate, time-to-first-appointment, completion of care plans.
- Clinician efficiency: documentation minutes per encounter, reuse of templates, rework rates.
- Revenue integrity: clean claims, denial rates, and evidence trails for CoCM/BHI or private-pay models.
How to “Show Your Work” without Boiling the Ocean
Make measures first-class data, not attachments. Capture the raw score (e.g., PHQ-9 = 14), the instrument/version, who recorded it, and the timestamp—every time. Store sessions as records that point to a living treatment plan and specific goals, so progress naturally rolls up over weeks (not via quarterly spreadsheets).
The rule of thumb: anything a clinician or patient enters should be queryable later without opening a PDF.
Then make rollups useful for operators, not just pretty. Cohort views by diagnosis, program, and payer should be one click from the dashboard and tied to staffing, scheduling, and roadmap choices (e.g., “group CBT slots cut no-shows 18% in Medicaid MCOs—double them”).
And log the “boring” artifacts—consent updates, audit trails, and crisis escalations—as first-class events too. When a risk screen triggers a 988 protocol, the system should auto-record the escalation path and acknowledgments. Boring is what survives audits—and gets you paid.
Anti-Goals (cut early, cut often):
- Feature bingo. If it doesn’t move symptoms, attendance, clinician time, or reimbursement, it’s a backlog item.
- Vanity KPIs (monthly active users, generic “engagement”). Behavioral health needs clinical and operational signals, not growth-app metrics.
The punchline: a behavioral health platform is measured by patient outcomes you can defend, not the number of screens you shipped. With that lens on, the next step is choosing a care model and scope that your budget—and your licensure and reimbursement realities—can actually support.
Define Scope and Care Model before Code
When you’re creating a behavioral health platform, lock the clinical lanes and operating footprint first—or you’ll rebuild billing, licensure, and supervision logic three times in the next 12 months.
Scope drives everything: who can treat whom (and where), which notes and consents you must capture, and whether payers will reimburse you at all.
Pick Your Clinical Lanes
- Therapy platform (psychology): If you plan multi-state telepsych, design around PSYPACT; it now spans much of the U.S. and dictates how doctoral-level psychologists practice across state lines. Build state-aware scheduling, eligibility checks, and consent flows off the PSYPACT map.
- Counseling platform (LPC/LMHC): The Counseling Compact has been enacted in dozens of states and expects to start granting privileges in 2025—bake compact-privilege verification into onboarding and renewals.
- Psychiatrists: For multi-state tele-psychiatry, plan around the Interstate Medical Licensure Compact (IMLC) and its participating-states list; your licensing logic should check compact status per provider and target state.
- Substance-use programs (SUD): Your data model must assume Part 2 segmentation from day one—separate authorizations, redisclosure rules, and purpose-of-use logging.
Choose Reimbursable Care Models Early
If you want reimbursement (not just cash-pay), anchor workflows to recognized models:
- Collaborative Care Model (CoCM) for primary-care-anchored BH: implement the three-person team (treating clinician, BH care manager, psychiatric consultant), registry-based follow-up with validated scales, and monthly time thresholds—then bill 99492/99493/99494 (+ G2214). Your product should track per-month minutes and registry touches, or you won’t pass audits.
- Group therapy and youth programs: If you’re running groups, align therapy sessions and daily limits with CPT 90853; enforce per-patient attendance/diagnosis linkage and session distinctness.
- General BHI outside CoCM: support 99484 or G0323 (for CP/CSW-led care) with initiating-visit checks, monthly minutes, and validated-scale storage.
Supervision, Guardians, and Care Coordination
- Supervision: Many counselors practice under supervision; model supervisor assignment, countersignature, and attestation as first-class objects—not free-text.
- Minors/guardians: Implement flexible consent (guardian/young adult), privacy modes for sensitive notes, and clear escalation paths for duty-to-warn.
- Care coordination: Build CoCM-style registries even if you’re not billing CoCM; they power measurement-based care and justify payer conversations later.
Quick Scope Matrix
| Lane | Interstate practice design | Reimbursable anchors | Data sensitivity you must model |
| Therapy platform (psychology) | PSYPACT verification + state routing | Psychotherapy codes; optional CoCM consult roles | Standard HIPAA; consent/versioning |
| Counseling platform (LPC/LMHC) | Counseling Compact privileges (2025+) | Psychotherapy & group codes; supervision artifacts | HIPAA; supervisor countersignature trails |
| Psychiatrists | IMLC license checks per state | E/M + psychotherapy add-ons; CoCM roles | HIPAA; med management auditability |
| SUD programs | State license + Part 2 segmentation | Group/family codes; case management | 42 CFR Part 2 consent and redisclosure controls |
Two guardrails before you spec features:
- If payers can’t map your workflows to codes, they won’t pay. Design UI around the time thresholds, team roles, and validated scales the codes require.
- If your licensure/compact logic is wrong, you can’t legally deliver care. Make compacts and state rules part of your access-control layer—not a policy wiki.
Implementation note: put HIPAA/Part 2 consent objects, audit logs, and role-based access in the data model now; bolting them on later is how platforms fail security reviews and get excluded from payer panels (more in Compliance below).
Minimum-Viable Clinical Workflows and Data Model
You’ve defined the loop and the care lanes. Now make it real with a lean data model that supports assessment tools, progress tracking, clinical documentation, treatment plans, and secure messaging—without painting yourself into an integration corner.
Model the Episode, Not Just the Visit
Anchor everything to an Episode of Care that links encounters, notes, plans/goals, and billing exports. Each encounter should be small, typed, and traceable (who/when/how). That’s what lets progress accumulate cleanly and makes EHR integration boring—in a good way.
Minimum Set (you can ship with this):
- People and access: Patient; Practitioner/Role; RelatedPerson for guardians; Consent and AuditEvent for changes.
- Assessments: Questionnaire + QuestionnaireResponse → scored Observation (progress tracking lives here).
- Visits: Appointment (schedule/attendance) and Encounter (what actually happened).
- Clinical documentation: Composition/DocumentReference for the note; template-friendly, structured fields.
- Treatment plans: CarePlan with linked Goal objects; notes and observations point back here.
- Ops and revenue: Coverage, Claim/ClaimResponse (or an export bundle your RCM can ingest).
- Secure messaging: a Conversation/Thread entity → Message (participants + pointers to Episode/Encounter).
FHIR Anchors (MVP) — Use This as the Build Ticket
| Workflow need | Must-have artifacts | FHIR anchors |
| Identity & permissions | demographics, guardian link, consent + audit | Patient, RelatedPerson, Consent, AuditEvent |
| Pre-visit assessments | instrument, score, timestamp, recorder | Questionnaire, QuestionnaireResponse → Observation |
| Visit logistics | time, modality, attendance | Appointment, Encounter |
| Note-keeping | structured note tied to plan/goals | Composition/DocumentReference, CarePlan, Goal |
| Billing export | codes, time, diagnosis link, coverage | Encounter, Coverage, Claim (+ ClaimResponse) |
| Progress tracking | longitudinal score deltas, goal status | Observation (time series), Goal/CarePlan status |
| Communication | risk-aware secure messaging threads | Conversation/Thread, Message (+ references) |
Edge Cases (data implications only):
- Group care → Group + group Encounter; each participant gets a per-patient note reference.
- Minors/guardians → RelatedPerson + scoped Consent; optional “private note” sections with restricted access.
- Risk triggers → thresholded Observation spawns a Task and stamps an AuditEvent chain (escalation trail).
Interfaces That Keep It Tight
- Clinician view: today’s encounters, due/overdue assessments, active treatment plans/goals, unfinished notes.
- Patient portal: upcoming sessions, assessments to complete, plan overview, secure messaging.
- Interoperability first pass: start with Observation, Composition/DocumentReference, CarePlan/Goal, Encounter; add more only when a partner system needs it.
Compliance You Can’t Fake
If your platform can’t prove what happened—policy → control → audit logs—it didn’t happen. Treat compliance as product UX for regulators: fast to inspect, boring to approve. This is behavioral health software development, not a slide deck.
What “Good” Looks Like (minimum compliance architecture)
Think in five layers. Ship these early, not in sprint 19.
1. Identity and Access (security starts here)
Role-based + attribute-based access (RBAC + ABAC). Least-privilege by default. Break-glass with reason code, supervisor notification, and automatic log capture. Quarterly access reviews built into the admin UI.
2. Data Classification and Consent
Label every record as PHI / non-PHI and Part 2 or not. Consent is a first-class object that gates reads/exports. When consent changes, future access reflects it; past patient data access remains auditable.
3. Segmentation for 42 CFR Part 2
Part 2 data travels on a separate rail: distinct scopes, stricter sharing rules, and redisclosure barriers. Enforce at query time (policy engine) and at rest (separate keys/partitions). Exports pass a consent/“minimum necessary” check before leaving the system.
4. Transport and Storage Protections (HIPAA compliance controls)
TLS in transit; encrypted at rest with managed keys and rotation; per-tenant isolation; secrets in a vault; automated backups + tested restores. No third-party trackers in PHI views. LLMs never see raw PHI unless you’ve built a de-identification gateway and a signed BAA specifically for that use.
5. Observability you can take to an audit
Tamper-evident audit trails for: auth events, consent updates, record views/edits, exports, policy decisions, break-glass, and 988 escalations. Logs are write-once (or WORM-style), time-synced, and queryable by patient, user, and time window.
Check out our notes on HIPAA compliant app development for a deeper dive.
BAAs without Regrets
Sign Business Associate Agreements with anyone who can touch PHI: cloud/IaaS, video, SMS/email, eFax, error logging, analytics, support desk, file storage, backups, and any AI vendor. Inventory subprocessors, verify data residency, and document data flows. If a vendor won’t sign a BAA, they don’t touch PHI—period.
Interstate Practice is Policy-Driven, Not Wiki-Driven
You already mapped licensure/compacts earlier; now wire it into the system. A policy engine should read provider privileges and patient location before encounter creation or messaging is allowed. No green status, no care. (State maps and compacts live in your config, not in someone’s memory.)
Crisis (988) and Duty-to-Warn Are Workflows, Not PDFs
Risk screens that cross thresholds create a Task, route to on-call, and lock a structured escalation checklist (contact → response → follow-up). Each step writes immutable audit logs. If duty-to-warn is triggered, the disclosure gets its own record and redisclosure notices are enforced automatically.
Privacy by Design
- Short session timeouts for shared devices; re-auth for sensitive actions.
- Private-note sections (restricted audience) for sensitive encounters.
- Download guardrails: watermarked PDFs, scoped exports, and optional data loss prevention on copy/paste for admin consoles.
- “Minimum necessary” defaults in clinician search and reports.
Proof Pack (what you should be able to produce on request)
- Current BAA list + data-flow diagram.
- Access-review report with exceptions resolved.
- Consent history for a patient, including redisclosure limits.
- Break-glass events with reasons and supervisor acks.
- 988 escalation trail for a specific encounter.
- Backup/restore evidence (last test run).
- Security risk analysis with remediation tickets linked.
Bottom line: build privacy, security, consent, and audit logs into the platform just like scheduling or notes. Do it now, when changes are cheap. In the next section, we’ll map these controls into a reference architecture so your engineers know exactly where each piece lives.
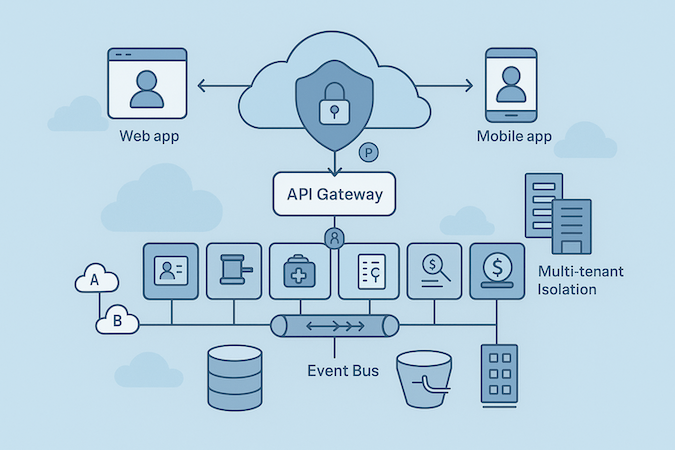
Reference Architecture for BH Platforms
You’re not building pages; you’re building plumbing. The target shape of a digital behavioral health platform looks like this: cloud-based, horizontally scalable, secure by default, and boring to operate.
The Frame (keep it small, make it scale)
- Clients: Web + mobile talk to an API gateway (REST/gRPC). Feature flags at the edge.
- Auth and policy: IdP (OIDC) → short-lived tokens, mTLS inside the cluster, zero-trust with a policy engine (RBAC + ABAC) evaluating every call.
- Core domain services (start modular, split later): Identity, Consent/Policy, Scheduling, Encounter, Assessments, Plans/Goals, Notes, Billing, Messaging. Begin as a modular monolith; peel into microservices only where you hit independent scale/failure domains (e.g., video, messaging, billing exports).
- Integration layer: Async adapters for EHR (FHIR), payments, comms (SMS/email/video), analytics. Everything through an event bus so retries and back-pressure don’t wake you at 3 A.M.
Multi-Tenant Isolation (pick one, don’t improvise)
- Row-level security: Fastest to ship; strict policy checks + per-tenant keys.
- Schema-per-tenant: Cleaner blast radius, moderate ops overhead.
- Database-per-tenant: Best isolation, highest cost/ops.
Encrypt per tenant; isolate file/object storage paths; make exports tenant-scoped by construction.
Data Stores (use two on purpose)
Relational (e.g., Postgres)
Appointments, Encounters, CarePlans/Goals, Claims—anything you report/join often.
Document/objects
Notes (Composition/DocumentReference payloads), attachments, message bodies, audit trails.
Add a log/metrics store for observability; keep PHI out of queryable traces unless the store is covered by a BAA.
Resilience and Operations
- DR/BCP: Multi-AZ baseline; RPO ≤ 15 min, RTO ≤ 1 hr for core API. Nightly backup drills and quarterly restore tests.
- Secrets management: KMS + a vault; rotate app and DB creds; no secrets in env files.
- Scalability: Stateless services behind autoscaling; queues for bursty work; pre-warmed workers for video/scheduling spikes.
- Security: WAF at the edge, allow-list egress, dependency scanning in CI, signed images, least-privileged IAM everywhere.
- Observability: SLOs per domain (e.g., note save ≤ 200 ms p95). Correlate logs/traces/metrics by request ID; audit streams are append-only/WORM.
Migration Path (so you don’t rewrite in year two)
- MVP: modular monolith + event bus + two stores.
- Scale: split Messaging, Assessments scoring, and Billing exports into services; add read replicas.
- Multi-region: active-passive for API; active-active for static assets and messaging.
Need a team that’s built this plumbing before? Our healthcare app developers can help without turning it into an endless platform rewrite.
Net: keep the core tight, isolate tenants, push integrations through the bus, and treat security as a runtime policy—not a wiki page. That’s architecture you can ship and safely evolve.
Core Feature Set by Phase (MVP → Scale)
Feature bingo kills timelines. Ship the care loop first, then layer revenue and scale.
MVP: 6–12 Weeks
Ship only what a clinic can run tomorrow:
- Video conferencing: 1:1, HIPAA-ready; reuse your telemedicine app development playbook for reliability.
- Appointment scheduling + SMS/email reminders; no-shows tracked.
- Intake & assessments: PHQ-9/GAD-7 pre-visit; raw scores stored.
- Clinical documentation: SOAP templates, required fields, e-sign.
- Treatment plans & goals linked to each encounter.
- Patient portal: upcoming sessions, assessments, secure messaging.
- Billing/insurance: superbill or basic claims export; card-on-file.
- Crisis management: threshold flags → on-call task + timestamped log.
Scale: 3–9 Months
Expand services, proof, and cash flow
- Groups & peer support with moderation and attendance.
- eRx partner for med management (psychiatry lanes).
- RCM depth: eligibility (270/271), claims/ERAs (837/835), denial workflows.
- Outcomes dashboards: cohort trends by program/payer; goal attainment.
- Care-team workflows: CoCM registry, role routing, time tracking.
- Content & self-help resources; multilingual & accessibility polish.
- Scheduling at scale: waitlists, load balancing, provider licensure checks.
- Payments: plans, subsidies, refunds; ledger-grade reporting.
Cut list (for now): gamification, community marketplaces, and custom analytics UIs—until they move outcomes, throughput, or collections.
This is the MVP track for behavioral health app development: video, scheduling, assessments, notes, plans, messaging, basic billing—then groups, eRx, full RCM, and real outcomes reporting.
Interoperability Playbook (EHR and beyond)
You can’t develop behavioral health platform without explicit HL7 FHIR mapping—interoperability isn’t a switch, it’s the backbone of your care loop. Start from concrete resources, then decide how deep you’ll write back.
The Three-Lane Plan
Lane 1 — Read-Only (fast, safe)
Pull Questionnaire/QuestionnaireResponse → score to Observation; fetch Encounter summaries and prior notes via DocumentReference/Composition; respect Consent on every call. This gives clinicians context without risking chart pollution.
Lane 2 — Targeted Write-Back (MVP+)
Write Observations (e.g., PHQ-9 deltas), attach structured notes as DocumentReference, and post Encounters tied to CarePlan/Goal. Keep SUD data segmented; never auto-push 42 CFR Part 2 content without a purpose-of-use check.
Lane 3 — Operational Integration (scale)
Scheduling (Appointment) with attendance updates; Subscriptions for eventing; identity via MPI/EMPI; revenue flows through X12 rails (270/271 eligibility, 837 claims, 835 ERAs) while keeping payment processing PCI-only—no PHI in your PSP.
Vendor Tactics That Actually Ship
- Epic: Lead with SMART on FHIR + OAuth2/PKCE; begin read-only, then add Observation/DocumentReference writes. Some workflows (advanced scheduling, inbox) still require non-FHIR APIs—plan an adapter and throttling.
- Oracle Cerner: Millennium FHIR first; watch per-tenant rate limits and use Subscriptions/Webhooks where available.
- athenahealth: Mix of FHIR and proprietary REST; good for appointment/claims pipes, but model backoffs and retries.
Auth and Policy Guardrails
SMART-on-FHIR for EHR-launched context; Backend Service auth for system-to-system jobs. Every write gates through consent and role policy; audit each request (who/what/why). Keep tokens short-lived; rotate client secrets.
What to Ship First (and why)
- Read-only context (QuestionnaireResponse → Observation, prior DocumentReference, current CarePlan/Goal).
- Targeted write-back of Observations + signed note DocumentReference.
- Scheduling + claims pipes once ops are ready.
Pitfalls to Dodge
- Mixing PHI into payment processing metadata. Don’t.
- Unsegmented SUD notes leaking to EHR portals.
- “One big integration.” Use an event bus and small, testable adapters.
For deeper EHR integration patterns (including concrete FHIR bundles), see our EHR integration guide. If you’ll ingest vitals from wearables, align your Observation profiles early with your RPM data model; see remote patient monitoring.
Safety and Risk Management by Design
Safety isn’t a policy wiki; it’s runtime behavior. Design it like a control system: detect → decide → act → document.
Detect
- Screen scores + trend breaks trigger risk signals; add lightweight language flags in secure messaging for self-harm/violence terms (respect privacy scopes).
- Nonbehavioral signals matter too: repeated no-shows, abrupt care-plan drop-offs, failed check-ins.
Decide
- A policy engine evaluates location, licensure, consent, and minors/guardians status, then selects the right intervention playbook (on-call, community resource, supervisor review).
- Rate-limit dangerous interactions (spam, harassment) before a human reviews.
Act
- One-tap warm handoff to on-call; auto-offer geofenced resources (hotlines, crisis centers) based on patient location.
- In groups, enable moderation tools: pause thread, hide harmful content pending review, remove/ban users, and lock DMs when risk is active.
Document
- Every step emits immutable audit events: trigger → decision → responder → outcome.
- Store sensitive notes in restricted sections; partition Part 2 content by default.
Community Hygiene (small features, big impact)
- Join gates (program eligibility + code of conduct), first-post review, keyword queues, block/report, and cooling-off timers for heated threads.
Bottom line: when you build mental health platform features, wire safety into flows—not post-hoc. Crisis management, timely intervention, protected privacy, and operational moderation are table stakes for trust and scale.
Build vs Buy vs Assemble (reusable HIPAA components)
In behavioral health platform development, the strategic call isn’t “custom or vendor?”—it’s assemble: keep your differentiation custom, snap in HIPAA-ready commodities.
| Option | When it wins | Time-to-Value | 3-Year TCO (directional) | Key Risks | BAA/Compliance Lift | Keep Custom (Examples) |
| Buy (full platform) | You need operations live yesterday; limited differentiation | Fastest (weeks) | High (licenses + change fees) | Vendor roadmap lock, data/UX inflexibility | Vendor BAAs mandatory; limited control | Care model nuances, outcomes analytics, FHIR mappings often constrained |
| Build (100% custom) | You have unique workflows + funding + in-house ops maturity | Slowest (9–18 mo) | Highest (eng + ops) | Schedule risk, talent churn, maintenance debt | You own all BAAs, audits, security | Everything—high risk of reinventing commodity parts |
| Assemble (recommended) | You need speed and control; commodity parts exist | Fast (6–16 wks) | Medium (dev + vendor modules) | Integration seams, vendor swap costs | Split: BAAs for each module + your core | Differentiated UX, care pathways, outcomes, policy engine; plug-in video, messaging, payments, eFax, eRx |
Heuristic (use this and move on):
- If it’s regulated plumbing (video, eFax, SMS, payments, IDV), assemble with vendors that sign BAAs.
- If it’s how you practice (care flows, policy/consent logic, outcomes views), build it.
- Revisit TCO vs. revenue quarterly; kill modules that don’t pay for themselves. See healthcare app development cost for modeling.
Bottom line: optimize time-to-value with assembly, protect long-term TCO by keeping your secret sauce custom, and keep a clean vendor BAA inventory from day one.
Responsible AI (without tripping FDA)
In mental health technology, AI should make clinicians faster—not braver. Keep AI/ML behind the human, instrumented, and easy to audit. If you can’t explain what the model did, you shouldn’t ship it.
What’s Safe Right Now Is Boring and Valuable
Clinical documentation assist that drafts SOAP from audio or notes, careful summarization of long threads into billable, reviewable nuggets, and lightweight intake routing that prioritizes urgency without assigning diagnoses.
Add quiet quality checks that flag contradictions, missing consents, or risky language in secure messages. All of it speeds care; none of it makes the decision for the clinician.
Draw the Bright Line on CDS vs SaMD
If the output is transparent, source-linked, and a clinician can independently assess it before acting, you’re in non-device CDS. The moment the model drives or recommends clinical action that isn’t independently reviewable—or is aimed at patient self-use—you’ve drifted into SaMD territory and should expect FDA obligations. Default posture: assist, don’t direct.
Design Human-in-the-Loop Like a Real Control, Not a Checkbox
Every suggestion is accepted or edited by a named clinician; nothing patient-visible goes out without a human sign-off; an inline “why did the model say this?” panel cites the bits of evidence it used. Treat prompts, guardrails, and outputs as medical records’ cousins—versioned and attributable.
Lock Down PHI Handling
No PHI to vendors without a BAA; prefer on-tenant inference or de-identified payloads; strip identifiers at the gateway; keep only the minimum necessary artifacts and segregate them like any other patient data.
Finally, make it auditable and resilient: version models and prompts, log who used which version, red-team for prompt injection and unsafe advice, and fall back to “route to human” when confidence is low or policy checks fail. Start with documentation assist in one program, measure time saved and error reduction, then expand—deliberately.
How Topflight Can Help You Develop a Behavioral Health Platform
If you’re deciding how to build a behavioral health platform, we’ll keep you out of the hype and inside a working operation. Our approach is assemble-first (HIPAA-ready vendors for regulated plumbing) plus custom where your care model, user experience, and outcomes differentiate.
What You Get (operator-grade, not demo-ware)
Our experience in mental health app development carries straight into platform builds—same clinical rigor, just wider plumbing.
- Revenue-cycle wiring: eligibility, claims/ERAs, denial workflows—clean reimbursement signals tied to encounters, not spreadsheets.
- Billing/insurance that matches your contracts and payers; audit-ready exports and reports.
- Provider onboarding playbooks that shorten time to first clean note; role-based templates for mental health professionals (therapists, prescribers, care managers).
- Patient engagement built into the loop: assessments, reminders, secure messaging, and outcomes views that matter to programs treating anxiety, depression, or substance abuse.
- Web + mobile app UX that feels clinical (not consumer-y) and scales across your telehealth platform, teletherapy, and virtual therapy workflows.
Proof from the Trenches
These aren’t dribbble shots; they’re healthcare app development wins shipped under pressure.
- Mi-Life (group homes): HIPAA-compliant, AI-powered assistance with RAG, OTP auth, multi-tenancy; reduced errors, improved staff satisfaction, and readiness for a specialty EHR integration.
- XZEVN (web + mobile): AI-assisted mental health companion (PWA + native) using TensorFlow, NLTK, KNN/RBM to personalize content; shipped from validated UX to production across web platform and apps. specialty EHR integration.
- SoberBuddy (SUD recovery chatbot): took over a broken prototype, rebuilt cross-platform (Ionic→React/React Native), added a CMS for the decision tree and RevenueCat for subscriptions; outcomes: $1M raised, retention +300%, engagement +40%, rating 3→4.5, +30k users, CAC −50%.
How We De-Risk Delivery
- Assemble HIPAA components (video, messaging, eFax, payments) with BAAs; model TCO and vendor swap costs upfront.
- Keep your secret sauce custom: care pathways, policy/consent logic, outcomes analytics.
- Map FHIR early; run security reviews and log every decision (auditability by design).
Ready to build a behavioral health platform without drowning in integrations and rework? Let’s scope a pilot around your revenue cycle, engagement, and outcomes—and ship the first measurable win.
Frequently Asked Questions
How should we handle migrating data from legacy tools or an EHR into the new platform?
Treat it like a clinical safety project, not a CSV party. Map legacy fields to FHIR resources, run identity matching via EMPI, and backfill in phases (most recent encounters first). Dual-run for a sprint to compare outputs, keep read-only snapshots for audit, and don’t import anything you can’t provenance.
What's the pragmatic approach to BYOD and device security for clinicians?
Use MDM or app-level management with conditional access, require device encryption/biometrics, and block jailbroken/rooted devices. Enforce app attestation, short tokens, and server-side controls for copy/paste and downloads. Offline notes should be encrypted at rest and auto-synced with conflict resolution.
We serve multiple languages and cultures - how do we do that without breaking clinical quality?
Internationalize early: resource files, locale-aware dates/phones, RTL support, and translation memory. For validated instruments (PHQ-9, GAD-7), use official translations or run a forward–back translation with clinical review; don’t roll your own. Add interpreter handoffs and culturally appropriate crisis resources.
Any tips on payer contracting and credentialing timelines post-launch?
Start with eligibility checks and clean claims while you credential; out-of-network plus single-case agreements can bridge early revenue. Keep CAQH current, track panel status by payer and state, and bring a one-pager showing no-show reduction, documentation time cut, and early outcome deltas. Contracting moves faster when your data makes their actuaries comfortable.
What should our post-launch reliability and incident response look like?
Set SLOs per workflow (e.g., note save p95 ≤ 200 ms, video uptime ≥ 99.9%) and track error budgets. Run DR drills quarterly, chaos-test critical paths, and keep an on-call runbook with templated patient/provider comms. Every incident needs a timeline, root cause, and action items—then wire those fixes into CI gates so they don’t regress.