In the dynamic world of healthcare technology, understanding how to make software HIPAA-compliant is more than a necessity; it’s a mandate. Our comprehensive guide serves as a beacon for those navigating the intricate waters of HIPAA compliance in software development, debunking common myths, highlighting the significance of adhering to this essential legislation, and providing actionable insights that you can immediately implement in your organization.
Top Takeaways:
- The Art of HIPAA-Compliant Software Development: Have you ever wondered what makes healthcare technology truly reliable? The answer lies in HIPAA-compliant software development. This guide delves into the importance and process of creating software that adheres to HIPAA regulations, ensuring that patient data is always protected. It’s not just about coding; it’s about integrating security measures at every step, from design to deployment.
- Empower Your Software with HIPAA Compliance: So, you have a functional health app. But is it HIPAA-compliant? If not, this guide provides insights on how to make your software HIPAA-compliant. Moving beyond the buzzwords and jargon, it offers a step-by-step approach to understanding and implementing key HIPAA provisions like the Privacy Rule, Security Rule, and more. It’s about turning your software into a safe haven for sensitive patient data.
- Navigating the Challenges of HIPAA Compliance: Let’s face it – achieving HIPAA compliance in software development can feel like navigating a maze. But with our guide, you’ll be equipped to overcome common hurdles such as understanding complex regulations, conducting regular risk assessments, and fostering a culture of compliance within your team. Remember, every challenge is an opportunity to strengthen your software’s security and enhance user trust.
Table of Contents:
- Purpose and Importance of HIPAA in the Healthcare Industry
- HIPAA’s Impact on Software Development for Healthcare
- Key Provisions of HIPAA
- Common Myths about HIPAA Compliance
- HIPAA Compliance Challenges in Software Development
- Best Practices for HIPAA-Compliant Software Development
- Data Privacy and Security Management
- Regulatory Compliance and Documentation
- Real-World Consequences of Non-Compliance
- Impact of New Technologies on HIPAA Compliance and Future Trends
- HIPAA Compliance Tools and Resources
- HIPAA Compliance Checklist
- Topflight’s HIPAA-compliant Software Development Case Studies
Purpose and Importance of HIPAA in the Healthcare Industry
In the rapidly evolving world of healthcare, the importance of data security cannot be overstated. This is where the Health Insurance Portability and Accountability Act (HIPAA) comes into play. The enactment of HIPAA introduced significant changes to how healthcare organizations handle, store, and use protected health information (PHI). But what does this mean for those involved in building a HIPAA-compliant software solution? Let’s delve into the purpose and importance of HIPAA in the healthcare industry.
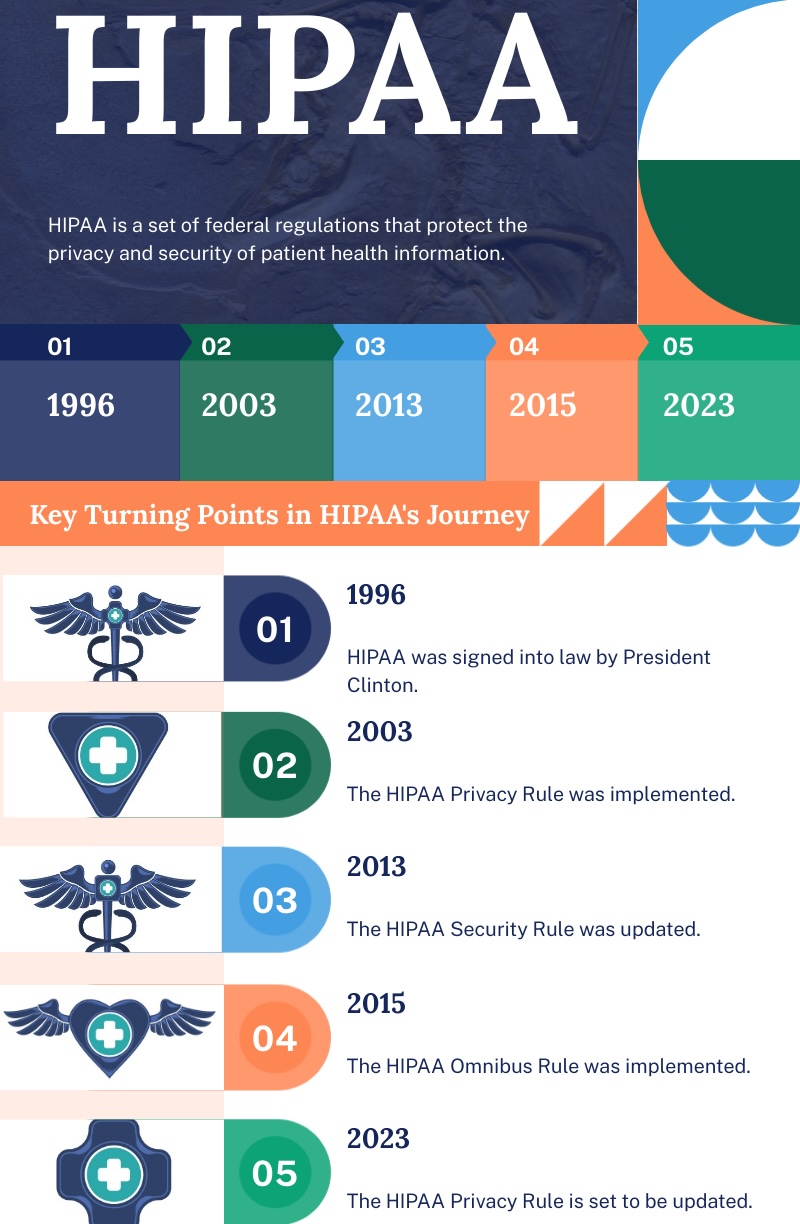
HIPAA is a federal law enacted in 1996 with the primary goal of safeguarding sensitive patient data. It establishes national standards for the protection of PHI, which includes a wide array of identifiable health information, from medical records to billing information. Today, HIPAA compliance is not just a legal requirement; it’s a fundamental factor in establishing trust between patients and healthcare providers.
Given the rise of digital health records and telemedicine platforms, the need for secure means of managing PHI has never been higher. This is where HIPAA-compliant software development comes in. To see an even deeper dive into architecture, controls, and pitfalls — and to guide your team step-by-step — hop over to our HIPAA compliant software development roadmap.
Developing software that complies with HIPAA regulations is essential for any entity that deals with PHI, including healthcare providers, health plans, and healthcare clearinghouses. To further understand how to develop a telemedicine app that’s HIPAA compliant, we recommend reading our detailed guide.
Developing HIPAA-compliant software involves implementing robust security measures such as encryption, access controls, and audit trails to prevent unauthorized access or disclosure of PHI. It ensures that sensitive health data is not only stored securely but is also accessible only to authorized personnel.
HIPAA-compliant software development serves multiple critical purposes in the healthcare industry:
- Protection of Sensitive Patient Data: HIPAA-compliant software helps protect sensitive patient information, ensuring that this data remains confidential and secure.
- Trust and Confidence Building: By complying with HIPAA, healthcare providers demonstrate their commitment to protecting patient privacy and fostering trust and confidence in their services.
- Legal Compliance: Failure to comply with HIPAA can lead to severe penalties, including hefty fines and potential legal action. HIPAA-compliant software helps healthcare providers stay within the boundaries of the law.
- Facilitation of Data Sharing: With the rise of digital health records and telemedicine, secure data sharing is crucial. HIPAA-compliant software enables secure exchange of patient information, enhancing collaboration among healthcare entities.
HIPAA’s Impact on Software Development for Healthcare
When we talk about the intersection of healthcare and technology, it’s impossible to ignore the profound influence of the HIPAA legal framework. Since its inception, HIPAA has significantly shaped the landscape of software development in the healthcare industry. But what does it mean for those involved in HIPAA compliance for software development?
HIPAA Evolution
To understand this, let’s briefly revisit the evolution of HIPAA. Established in 1996, HIPAA aimed to streamline health information flow, reduce fraudulent activities, and, most importantly, protect patient privacy. However, the full implementation of HIPAA did not occur until 2003, when the need for enforcement standards became apparent due to the increasing digitization of health records.
As technology advanced, so did HIPAA, proving its relevance and significance in our increasingly digital world. In 1999, the Department of Health and Human Services proposed the Privacy Rule, which required HIPAA covered entities to comply by April 2005. This rule was a critical step toward ensuring the protection of patient PHI in the era of EHRs.
Over the years, HIPAA has indeed evolved to encompass more than originally intended. Today, it covers a wide range of entities within the healthcare industry and has adapted to new challenges and technological advancements, such as the advent of cloud computing and telemedicine. For instance, a HIPAA-compliant video conferencing API can ensure safe and confidential patient-doctor interactions.
How HIPAA Affects Health App Development
The implications of HIPAA compliance software development are vast and varied. It sets the benchmark for protecting sensitive patient data, ensuring its confidentiality, integrity and availability – the “CIA triad.”
Any software that handles protected health information must adhere to these stringent standards.
This is where the importance of HIPAA training comes into play. It’s crucial for software developers to understand the ins and outs of HIPAA regulations. Training equips them with the knowledge to incorporate the necessary privacy and security measures during the software development lifecycle, thereby reducing the risk of data breaches.
Remember, HIPAA covers a wide range of entities within the healthcare industry, including:
- healthcare providers
- health plans
- healthcare clearinghouses
If you’re developing software for these entities, HIPAA compliance isn’t an option – it’s a requirement.
And who ensures this compliance? Enter the Office for Civil Rights (OCR). Tasked with enforcing HIPAA regulations, the OCR conducts audits and investigates potential violations. Non-compliance can lead to hefty penalties and legal consequences. Therefore, prioritizing HIPAA compliance safeguards not just patient data but also the reputation and financial stability of your organization.
As you understand, the impact of HIPAA on software development for healthcare is profound and far-reaching. It necessitates a holistic approach to protecting patient data, involving careful planning, rigorous training, and robust security measures.
Key Provisions of HIPAA
Understanding HIPAA is crucial for anyone involved in the healthcare industry, especially for those developing software. HIPAA for software developers is not just about knowing what HIPAA is but grasping the key provisions that directly impact how software should be developed to ensure HIPAA compliance.
So, what makes software HIPAA-compliant?
1. HIPAA Privacy Rule
The HIPAA Privacy Rule is a critical provision that governs the use and disclosure of individuals’ protected health information. It sets limits on how healthcare providers and other covered entities can use and share patient data. As a software developer, it’s essential to ensure that your applications adhere to these privacy requirements to protect patient privacy.
2. HIPAA Security Rule
The HIPAA Security Rule complements the Privacy Rule by outlining specific safeguards for electronic PHI (ePHI). It mandates that covered entities and their business associates implement administrative, physical, and technical safeguards to protect ePHI from unauthorized access, use, or disclosure. As a software developer, incorporating these security measures into your app is essential for HIPAA compliance.
3. Breach Notification Rule
The HIPAA Breach Notification Rule requires that covered entities notify affected individuals, the Secretary of Health and Human Services, and, in some cases, the media in the event of a breach of unsecured PHI. As a software developer, understanding the requirements for breach notification and designing your applications to detect and respond to potential breaches promptly is crucial.
4. Business Associate Agreements (BAAs)
Under HIPAA, covered entities must have written agreements with their business associates, who are individuals or organizations that perform services involving the use or disclosure of patient data. As a software developer, if you handle personal health data on behalf of a covered entity, you may be considered a business associate. It’s crucial to have BAAs in place to ensure compliance.
5. HIPAA Enforcement and Penalties
HIPAA violations can result in significant penalties, including fines and criminal charges. The Office for Civil Rights is responsible for enforcing HIPAA compliance. As a healthcare app developer, being aware of the potential consequences of non-compliance and ensuring that your software meets the necessary HIPAA requirements can help avoid legal and financial repercussions.
Incorporating these key provisions into your healthcare app development process is vital to creating HIPAA-compliant healthcare applications. By understanding the HIPAA rules and designing your applications to comply with them, you can contribute to the secure and responsible handling of patient data, ensuring the privacy and security that is paramount in today’s digital healthcare landscape.
Common Myths about HIPAA Compliance
When it comes to developing HIPAA-compliant software, it’s essential to cut through the noise and debunk common myths surrounding HIPAA compliance. Misconceptions can lead to confusion, non-compliance, and even penalties. So, let’s set the record straight and provide clarity on what it really means to make a HIPAA compliant software solution.
Myth 1: Making a HIPAA Compliant Software is an Overwhelming Task
While adhering to HIPAA regulations does require attention to detail, it’s not an insurmountable task. With the right approach, understanding of the law, and adherence to best practices, developers can create software that meets HIPAA requirements and safeguards patient data effectively.
Myth 2: Only Covered Entities Need to Comply with HIPAA
It’s not just covered entities like healthcare providers who need to comply with HIPAA. Business associates, including software developers who handle protected health information (PHI) on behalf of these entities, also have compliance responsibilities. This underscores the importance of building a HIPAA-compliant software tool across the board, not just within healthcare institutions.
Myth 3: User Authentication is All You Need for HIPAA Compliance
While user authentication is a key component of HIPAA compliance, it’s not the only one. HIPAA mandates a robust suite of safeguards, including access controls, encryption, audit logs, and more. It’s about creating a comprehensive security framework to protect PHI from unauthorized access, use, or disclosure.
Myth 4: Once Software is HIPAA Compliant, It Remains So Indefinitely
HIPAA compliance isn’t a one-time achievement; it’s an ongoing commitment. As technology evolves, so do potential threats, necessitating regular assessments and updates to ensure continued compliance.
Myth 5: HIPAA Compliance is Only Necessary for Software That Directly Handles PHI
HIPAA extends beyond applications that directly handle patient data. Any software that interacts with covered entities or handles PHI in any capacity must comply with HIPAA regulations. This includes applications that store, transmit, or process PHI on behalf of covered entities.
By debunking these common myths, we can better navigate the complexities of HIPAA compliance and create software solutions that truly respect and protect patient privacy. Remember, when it comes to developing HIPAA-compliant software, knowledge is power. Stay informed, stay compliant, and stay ahead.
HIPAA Compliance Challenges in Software Development
Navigating the path of HIPAA custom software development can be a complex journey filled with unique challenges. While the rewards are plentiful, it’s essential to understand and anticipate these obstacles to ensure your software meets all the necessary regulations and safeguards patient data effectively.
1. Understanding and Implementing Complex Regulations
One of the primary challenges in developing a HIPAA-compliant app is understanding the intricate web of regulations. HIPAA rules are complex, and their interpretation can vary. Therefore, it’s crucial for developers to have a thorough understanding of these regulations and how they apply to their software.
#ProTip: Keep in mind that HIPAA regulations apply not only to the finished software product but also to the processes involved in the development and maintenance phases—it’s an all-encompassing framework.
2. Regular Risk Assessments
HIPAA requires regular risk assessments to identify potential vulnerabilities and threats to PHI leaks. These assessments can be time-consuming and require expert knowledge to conduct effectively. However, they’re an essential part of maintaining HIPAA compliance and ensuring the security of your software.
#ProTip: Employ automated log audits to simplify periodic checks and maintain compliance standards. By leveraging automation, developers can streamline the process of reviewing access logs and identifying unusual patterns or discrepancies that may point to security risks.
3. Developing Comprehensive Policies and Procedures
Developing comprehensive policies and procedures is another significant challenge in HIPAA compliance. These policies should cover everything from user access controls to breach notification procedures. Not only do these need to be thorough and compliant with HIPAA rules, but they also need to be regularly updated to reflect changes in technology or regulatory requirements.
A cornerstone of maintaining HIPAA compliance is adhering to the Minimum Necessary Rule. This rule stipulates that PHI should only be accessed on a need-to-know basis, ensuring that only the minimum amount of information necessary for a specific task is used or disclosed.
#ProTip: To effectively implement the Minimum Necessary Rule, incorporate role-based access controls (RBAC) within your software. RBAC ensures that individuals are granted access rights strictly based on their role and responsibilities, limiting their access to PHI to what is essential for their job functions.
4. Ensuring Data Privacy and Security
Data privacy and security are at the heart of HIPAA compliance. Ensuring that your software can securely store, process, and transmit PHI is a considerable challenge, especially with the increasing sophistication of cyber threats. This necessitates implementing robust security measures like encryption, secure user authentication, and regular security audits.
#ProTip: Embrace a ‘hacker mindset’ by periodically engaging in penetration testing, sometimes referred to as ethical hacking. This proactive strategy involves attempting to breach your own health application’s defenses to assess the efficacy of security measures. By successfully identifying and exploiting vulnerabilities before a malicious actor does, you can ensure a more robust level of data privacy and security for patient information. Remember, if you can’t break into your own system, chances are, it will be much harder for someone else to do so.
5. Training and Awareness
Lastly, ensuring that everyone involved in the software development process understands the importance of HIPAA compliance and how to achieve it is a challenge. This involves regular training and awareness campaigns to keep everyone updated on the latest regulations and best practices.
By understanding these challenges and planning for them, you can effectively navigate the complexities of HIPAA compliance and create a secure, successful healthcare app.
Best Practices for HIPAA-Compliant Software Development
The road to HIPAA compliance in software development is filled with complexities, but with the correct guidelines, it can be navigated successfully. Following the HIPAA software development guidelines ensures not only that your product is legally compliant but it also gives your users confidence that their sensitive health information is safe and secure.
In this section, we will explore some of the best practices that should be followed when developing software that meets HIPAA compliance standards.
1. Incorporate HIPAA Compliance from the Start
HIPAA compliance should not be an afterthought—it should be embedded in the software development process from the very beginning. This approach, known as ‘Privacy by Design,’ ensures that privacy and data protection are integral to system designs and business practices. It’s far easier and cost-effective to build HIPAA compliance into your software from the start than to retrofit it later.
To get an idea about the medical app development cost, check out our comprehensive breakdown.
2. Implement Robust Data Encryption
One of the key HIPAA software development guidelines is to implement robust data encryption. Encryption transforms readable data into an unreadable format, which can be returned to its original form with a decryption key. All data, both at rest and in transit, must be encrypted to prevent unauthorized access.
3. Limit Access with Role-Based Permissions
Not everyone in your organization needs access to all data. Role-based permissions ensure that users can only access the data they need for their specific role. This principle, known as the ‘Minimum Necessary Rule,’ is a crucial part of HIPAA compliance.
4. Regularly Audit and Monitor Access
Regular auditing and monitoring of who accesses data and when is essential. This helps to quickly identify and respond to any unauthorized access or potential data breaches. Audit controls must be in place to record and examine activity in systems containing health information.
5. Engage with a Third-Party to Conduct a HIPAA Assessment
A third-party assessment can be invaluable in ensuring your software is HIPAA compliant. Independent auditors can provide an unbiased view and help identify any potential gaps in compliance that need to be addressed.
6. Run a Backup Plan
A key component of HIPAA-compliant software development is establishing a comprehensive backup plan to protect health information against loss due to unforeseen circumstances like hardware malfunctions, natural disasters, or cyberattacks. Consistent and secure backups are also imperative for data recovery, ensuring that patient data can be retrieved quickly and with integrity in case of any compromise.
7. Train Your Team
It’s important that your entire team understands the importance of HIPAA compliance and how they each play a role in maintaining it. Regular training should be provided to keep everyone up to date with the latest regulations and requirements.
8. Have a Plan for Breaches
Despite your best efforts, breaches can still occur. Having a plan in place for how to respond can limit damage and ensure you’re complying with HIPAA’s rules around breach notifications.
9. Keep Up with Changes
HIPAA regulations and technology are always evolving. It’s crucial to stay up-to-date with the latest changes to ensure ongoing compliance.
In conclusion, the software must meet the regulatory requirements set by HIPAA, but it’s also about building trust with the users by safeguarding their sensitive health information. By following these best practices from the start of the software development process, you can create a product that not only complies with HIPAA but also provides value to your users by keeping their data safe and secure.
Data Privacy and Security Management
In the domain of healthcare software, data privacy and security management hold paramount importance. As we build HIPAA-compliant software, we must always keep in mind that we are dealing with sensitive patient health information. This data is not only legally protected but also central to maintaining patient trust and confidence in our services.
The first step towards effective data privacy and security management is a thorough risk assessment. Regularly conducting these assessments helps identify potential vulnerabilities in your system, allowing you to address them proactively. For instance, a risk assessment might reveal that your software lacks sufficient access controls or that your data encryption protocols need strengthening.
When it comes to protecting provider and patient data, two-factor authentication (2FA) and multi-factor authentication (MFA) are your best friends. These security measures add an extra layer of protection by requiring users to provide two or more pieces of evidence (or factors) to authenticate their identity. This could be something they know (like a password), something they have (like a security token), or something they are (like a fingerprint). By implementing 2FA or MFA, you can significantly reduce the risk of unauthorized access to PHI.
Data encryption is another critical component of data privacy and security management. Encryption transforms readable data in cloud storage into an unreadable format that can only be deciphered with a decryption key. All PHI, whether at rest (stored) or in transit (being sent over a network), should be encrypted to prevent unauthorized access.
Finally, it’s crucial to keep your team informed and trained about the latest developments in data privacy and security. Remember, security isn’t just about having the right tools and protocols in place; it’s also about fostering a culture of data protection within your organization.
Regulatory Compliance and Documentation
Navigating the regulatory landscape of healthcare data can be a daunting task for many software developers. However, with the right approach and understanding, you can ensure that your application is in compliance with HIPAA.
Once you understand the Privacy and Security rules, the next step is to document your compliance efforts. This involves maintaining records of your risk assessments, privacy policies, employee training, and incident response plans, among other things. It’s also important to keep track of any changes in your practices or procedures that may affect the security of ePHI.
In addition, obtaining a HIPAA certification for software developers can be a valuable asset. This certification verifies that you have the knowledge and skills necessary to develop software that complies with HIPAA regulations. It also demonstrates to your clients and partners that you are committed to maintaining the highest standards of privacy and security in your applications.
To help ensure compliance with HIPAA, please consider keeping documentation for the following:
- Risk Assessments: Regularly conducted and thoroughly documented risk assessments help identify potential vulnerabilities in the protection of ePHI.
- Privacy Policies: Detailed policies outlining how ePHI is protected and used within the application.
- Incident Response Plans: Documented procedures for responding to potential breaches or incidents involving patient data.
- Employee Training Records: Proof that all developers and staff members have been trained on HIPAA compliance and understand their responsibilities.
- Access Controls: Documentation of user access controls ensuring only authorized individuals can access PHI.
- Audit Controls: Records of system activity, including hardware, software, and procedural mechanisms to record and examine access and other activity in systems that contain or use PHI.
- Transmission Security: Documents demonstrating the implementation of technical security measures that guard against unauthorized access to ePHI being transmitted over a network.
- Breach Notification Documentation: Procedures outlining how affected individuals and the Department of Health and Human Services will be notified in the event of a breach.
- Business Associate Agreements: If third-party vendors have access to ePHI, it’s crucial to have signed Business Associate Agreements (BAAs) on file.
- Data Backup and Disaster Recovery Plans: Documented procedures for backing up data and restoring any lost data in a disaster recovery scenario.
Real-World Consequences of Non-Compliance
Compliance with HIPAA requirements for software developers is not just a matter of best practice but a necessity. The real-world consequences for non-compliance can be severe, as seen in numerous cases from 2023.
Here are a few examples that highlight the dire consequences of not adhering to HIPAA regulations:
- Anthem Inc.: This major American health insurance provider faced one of the largest settlements to date, paying a whopping $16 million in 2023 after a cyberattack exposed nearly 79 million people’s private information.
- Premera Blue Cross: Another significant case involved this health insurer, which settled for $6.85 million following a cyberattack affecting over 10.4 million individuals. The breach exposed sensitive data, including names, addresses, dates of birth, email addresses, Social Security numbers, bank account details, and health plan clinical information.
- Memorial Healthcare System: This Florida-based healthcare system was fined $5.5 million for potential HIPAA violations involving unauthorized access to patient information by its employees.
- 21st Century Oncology: In a landmark case, this cancer care services provider agreed to a $2.3 million settlement due to potential violations of the HIPAA Privacy and Security Rules after the FBI informed them that patient information was illegally obtained by an unauthorized third party.
- University of Rochester Medical Center (URMC): URMC agreed to pay $3 million in penalties to OCR and take substantial corrective action to settle potential violations of the HIPAA Privacy and Security Rules. The organization reported that they lost an unencrypted flash drive and an unencrypted laptop that contained protected health information.
The trend of hefty fines didn’t end there. According to the Department of Health and Human Services, to date, OCR has settled or imposed a civil money penalty in 141 cases, resulting in a total dollar amount of $137,738,772.00. OCR has conducted investigations varying in severity and scope against a diverse assortment of entities, including national pharmacy chains, major medical centers, hospital chains, group health plans, and even small provider offices.
However, the consequences extend beyond financial penalties. Reputational damage can also be significant, leading to a loss of trust among patients and partners, which can be far more difficult to recover from than any monetary fine.
These real-life examples underscore the necessity of comprehensive understanding and adherence to HIPAA regulations. For software developers in the healthcare sector, it’s not just about creating functional and user-friendly applications but ensuring these applications meet stringent compliance requirements to protect patient data and avoid costly penalties.
Impact of New Technologies on HIPAA Compliance and Future Trends
In the rapidly evolving technology landscape, the role of HIPAA compliance for software developers is becoming increasingly intricate. New technologies continue to present both exciting opportunities and challenges in the realm of healthcare.
Take, for instance, the Internet of Medical Things (IoMT). Wearable devices like smartwatches and fitness trackers are transforming how we monitor health data. However, they also bring about new considerations for data storage and HIPAA compliance. Similarly, Software as a Medical Device (SaMD) presents another frontier, offering innovative solutions for diagnosing and treating patients but necessitating rigorous compliance protocols.
Read more on medical device software development
Here are some key trends to watch:
- Wearables and IoMT: These devices can collect a wealth of health data, from heart rate to sleep patterns. Ensuring this data is collected, stored, and transmitted securely is paramount.
- SaMD: As software increasingly plays a critical role in healthcare delivery, it’s essential to ensure these applications are developed and maintained with HIPAA compliance in mind.
- Telemedicine: This rapidly growing field requires robust data protection measures to safeguard patient information during virtual consultations. Our telemedicine app development services can help you leverage this trend while staying fully compliant with HIPAA.
- Artificial Intelligence and Machine Learning: These technologies offer immense potential for healthcare but also necessitate robust data protection strategies.
- Blockchain: While still in its early stages in healthcare, blockchain technology could offer new ways to secure health data, creating immutable records and enabling secure data sharing.
As we navigate these technological advancements, the need for medical software to be developed with HIPAA compliance at its core becomes even more pressing. It’s an exciting time to be a part of the healthcare tech industry, but as always, patient confidentiality and data security must remain our top priorities.
HIPAA Compliance Tools and Resources
As a HIPAA software developer in the healthcare sector, it’s crucial to have a strong understanding of the tools and resources available that can aid in ensuring HIPAA compliance. These resources not only help implement the necessary technical and administrative safeguards but also play a significant role in emergency access situations, ensuring that patient data can be accessed securely and promptly when needed.
Here’s a list of essential tools and resources that can be instrumental in your journey towards HIPAA-compliant software development:
- HIPAA Compliance Manuals: Comprehensive guides like the HHS’s HIPAA Survival Guide provide an in-depth look at the requirements for HIPAA compliance.
- Risk Assessment Software: Tools such as HIPAA One can help you conduct thorough risk assessments, a vital step in ensuring HIPAA compliance.
- Encryption Tools: Services like Virtru offer email and data encryption, helping protect sensitive health information in transit and at rest.
- Training Programs: Regular staff training is crucial. Resources like the HIPAA Training and Certification program can ensure your team is up-to-date on compliance requirements.
- Compliance Software: Platforms such as Accountable can help manage all aspects of HIPAA compliance, from training to document management.
Remember, these tools and resources are designed to assist you. However, the responsibility of achieving and maintaining compliance falls upon each organization. Ensuring HIPAA compliance is not a one-time event but an ongoing commitment to protecting the privacy and security of patient data.
HIPAA Compliance Checklist
A well-structured HIPAA compliance checklist for software development can serve as a roadmap, guiding you through each necessary step to ensure your healthcare application meets all the required standards.
Here’s a concise checklist to help you get started:
- Risk Assessment: Identify potential risks to ePHI (Electronic Protected Health Information) and assess their impact.
- User Authorization: Implement role-based access control (RBAC) to ensure only authorized individuals can access ePHI.
- Remediation Plan: Develop a plan to address any identified risks and vulnerabilities.
- Emergency Mode: Create procedures for accessing ePHI during an emergency.
- Encryption and Decryption: Implement encryption for all ePHI at rest and in transit.
- Audit Controls: Establish hardware, software, and procedural mechanisms to record and examine access and activity in systems containing ePHI.
- Data Backup Plan: Regularly back up ePHI and ensure it can be restored accurately.
- Data Integrity: Implement measures to confirm that ePHI has not been altered or destroyed unauthorizedly.
- Authentication: Validate that the person or entity seeking access is who they claim to be.
- Transmission Security: Protect against unauthorized access to ePHI being transmitted over a network.
- Automatic Logoff: Implement electronic procedures that terminate a session after a predetermined time of inactivity.
- Breach Notification: Have procedures in place to notify affected individuals, the Secretary of HHS, and, in some cases, the media of a breach of unsecured ePHI.
- Regular Audits: Conduct regular audits to assess the security of your ePHI.
- Employee Training: Provide training to all staff members about the security policies and procedures.
- Software Development Life Cycle (SDLC) and Testing: Follow secure SDLC practices and perform regular security testing on your application.
- Business Associate Agreements (BAAs): Enter into BAAs with any third parties that will access, transmit, or store ePHI on your behalf.
Remember, this checklist is a starting point. Compliance is not a one-and-done task. It requires continuous efforts, regular audits, and updates to keep up with changes in regulations and technology. Always consult with a legal expert to ensure you’re meeting all requirements. After all, when it comes to protecting patient information, there’s no room for guesswork.
Topflight’s HIPAA-compliant Software Development Case Studies
As experienced HIPAA-compliant software developers, we at Topflight have successfully delivered several projects that demonstrate our commitment to data security and compliance. Here are three case studies that highlight our expertise:
- Joovv: Joovv is a pioneer in the field of light therapy devices and needed a cutting-edge app to match their innovative hardware. The challenge was not only to revamp the design but also to enhance the app with advanced features while ensuring its HIPAA compliance.
- We developed a new app compatible with Joovv’s legacy devices and their latest hardware, effectively bridging the gap between software and IoT medical devices.
- The app was upgraded with engaging features such as goal setting, notification reminders, and session recovery to enhance user experience.
- To ensure HIPAA compliance, we implemented end-to-end data encryption at rest and during sync, secure user authorization via Amazon Cognito, and forced data transit over secure TLS/SSL connections.
- Dedica Health: A remote patient monitoring platform, Dedica Health allows healthcare providers to monitor patients’ vitals and provide care remotely.
- We implemented strong data encryption to protect patient health information during transmission and storage.
- Compliance with HIPAA regulations was maintained throughout the development process, ensuring the app could legally handle sensitive health data.
- Gale.ai: Gale.ai is an AI-powered app designed to streamline the medical coding process for billing.
- Leveraging machine learning algorithms, the app can accurately predict medical codes, increasing productivity and reducing errors.
- Throughout the development process, maintaining HIPAA compliance was a priority to ensure the secure handling of sensitive medical data.
Learn how AI in healthcare billing is reshaping traditional billing practices and bringing innovation to the forefront.
4. Stanford iFaint: This app, developed in collaboration with Stanford University, helps users track their fainting spells and share this information with their healthcare providers.
-
- We incorporated secure user authentication to prevent unauthorized access to personal health data.
- The app is equipped with features to ensure the secure transmission and storage of sensitive health data in line with HIPAA regulations.
These case studies underscore our commitment to developing high-quality, HIPAA-compliant software solutions. Whether it’s integrating with IoT devices or leveraging AI/ML technology, we understand the importance of maintaining the privacy and security of health information in all our projects. Our healthcare mobile app development services are designed with these strict guidelines in mind.
We hope this comprehensive guide has deepened your understanding of HIPAA compliance for software development; please don’t hesitate to reach out if you have any questions or need assistance with your project.
[This blog was originally published on 2/5/2024 but has been updated with more recent content]
FAQ
What are some key considerations in HIPAA compliant software development?
When embarking on HIPAA-compliant software development, it’s crucial to prioritize data privacy and security management. This involves encrypting protected health information (PHI), implementing user access controls, and conducting regular security audits. Additionally, an understanding of the regulatory requirements and documentation is essential, and adopting best practices such as privacy by design can streamline the process.
How can non-compliance with HIPAA impact an organization?
Non-compliance with HIPAA can have serious implications for an organization. Apart from hefty fines, it could lead to loss of reputation, legal action, and even business closure. It’s also important to remember that non-compliance can result in breaches that compromise patient data, leading to a loss of trust among consumers.
How do emerging technologies influence HIPAA compliance?
Emerging technologies, such as AI, machine learning, and blockchain, have a significant impact on HIPAA compliance. While they can enhance data security and improve healthcare services, they also present new challenges in maintaining patient privacy. Therefore, it’s crucial to constantly update compliance strategies in line with evolving technology trends.